Demo of Agama Linux Installer at OpenSUSE Conference 2025 – Nuremberg, Germany
Over the weekend at the OpenSUSE Conference 2025 in Nuremberg, Germany, I had the pleasure of showcasing Agama, the innovative new Linux installer set to debut in openSUSE Project Leap 16 and SUSE Linux Enterprise Server 16.
While still in active development, this tool is shaping up impressively and promises to redefine the future of unattended Linux installations.
Curious to learn more or get started? Explore the full documentation here:
https://agama-project.github.io/docs/user/
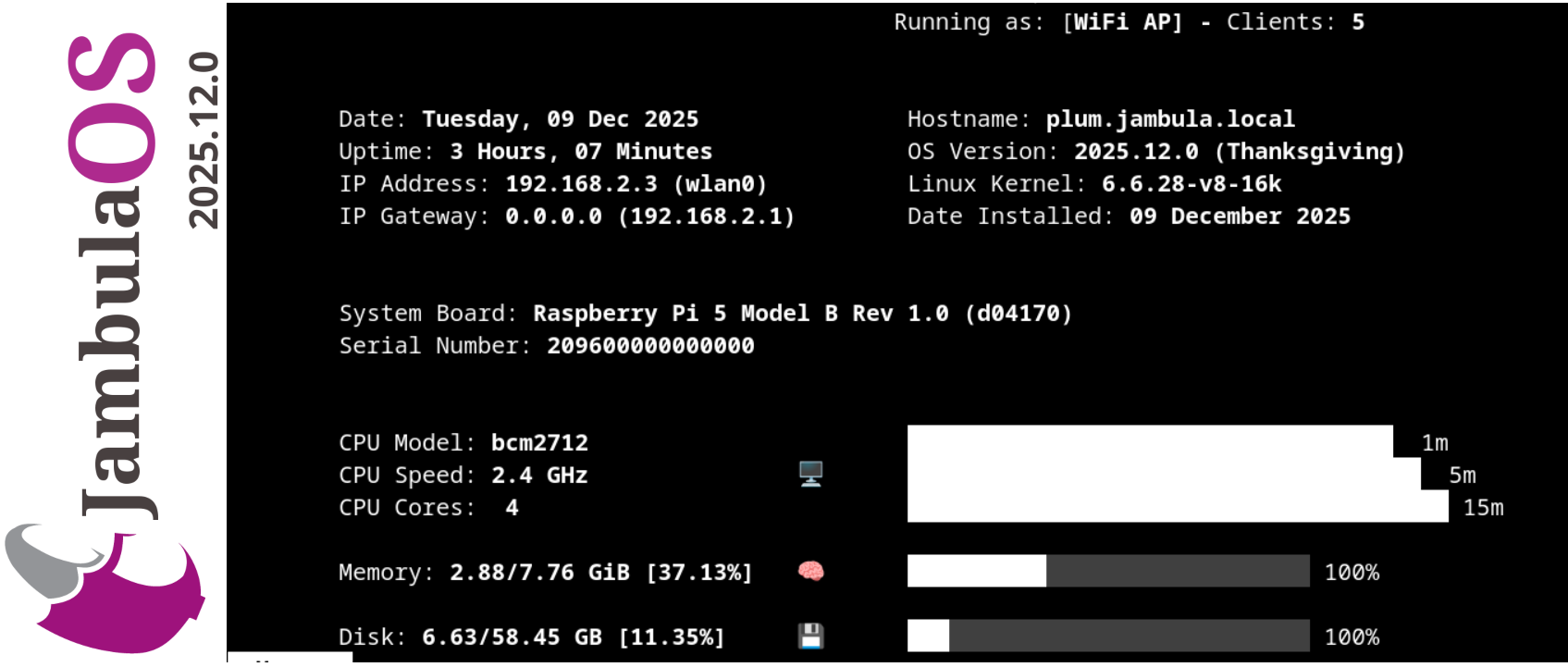
Jambula OS 2025.12.0 is Here! Now featuring a Robust, Cloud-Free, Private File Sharing Platform
I am excited to announce the immediate release of Jambula OS version 2025.12.0!
If you are a developer, a dedicated tech enthusiast, or a passionate DIY maker looking for a local and open smart home, this major release is built for you. Designed for the Raspberry Pi 5 and other SBCs, Jambula OS is the free, open-source Linux platform that I started with the goal of putting you back in control.
Do you already own a Raspberry Pi 5? Or perhaps you’re hoping that Santa listened closely this year? Either way, this major update makes it the perfect time to download the latest image of Jambula OS and transform your Pi into the brain of your next project.
What’s New in 2025.12.0
I focused on two main areas: making the system easier to use and making your data more private.
- Robust, Cloud-Free File Sharing and Collaboration: Tired of trusting your data to massive cloud providers? I included a Robust, Cloud-Free, Private File Sharing Platform in Jambula OS. Easily share documents and media privately with zero reliance on external cloud services. Your files, your rules.
- Complete Setup Menu Overhaul: I listened to your feedback! The new menus ensure a vastly improved initial setup and onboarding process, making the journey from flashing the image to running your first service smoother and faster than ever before.
- Home Assistant Version 2025.12.2: Your smart home deserves the best. This release ships with the latest Home Assistant version 2025.12, offering all the newest features of this world-class, local-first smart home platform.
For Valued Supporters: Enhanced Tools and Advanced Capabilities
To thank those who support the future of the Jambula OS project, I included a powerful suite of advanced tools in this edition:
Jambula Radio (In-House Smart Radio Broadcast): Discover how to listen to the radio the Smart way with this innovative, in-house solution.
A powerful, flexible NVR for intelligently organizing and monitoring your CCTV cameras, featuring optional AI integration..
Hotspot & Remote Access Tools: Comprehensive solution providing a robust Captive Portal for secure guest network access and specialized Managed Remote Access capabilities.
Features Available to All: Core Stability and Critical Performance
I’ve implemented several bug fixes and performance tweaks to ensure this is the most stable and reliable version of Jambula OS I’ve ever released.
Download Jambula OS 2025.12.0 Today!
https://jambula.org
#JambulaOS #IoT #DIY #RaspberryPi #Development #SmartHome #HomeAssistant #Linux #FOSS #OpenSource
Hass Core Installer Updated to 2025.12.2
A new version of Hass Core Installer is now available: 2025.12.2.
While this is a standard update, it includes a crucial fix for better stability:
- Home Assistant Core: Upgraded to the latest stable version, 2025.12.2.
- Bluetooth Management Fix: This version resolves the permissions error related to Bluetooth management (“Missing NET_ADMIN/NET_RAW capabilities”). I’ve updated the systemd unit to include the required NET_ADMIN and NET_RAW capabilities, ensuring smooth adapter recovery and operation.
You can grab the new installer and view the source code here: https://github.com/zikusooka/hass-core-installer
Jambula OS Has a New Home!
I am excited to share a major milestone in the Jambula OS journey. It’s official new home will now be at:
Jambula OS is a lightweight, fast and flexible free open source operating system built with one mission in mind: to empower creators, developers and communities. Whether you are building, experimenting or creating, Jambula OS is designed to give you the freedom and performance you need.
More Updates Are Coming
I have been working hard behind the scenes, and some major improvements and new features are on the way. Stay tuned – the next chapter of Jambula OS is going to be exciting!
Hass Core Installer 2025.10.3 Released
I have released Hass Core Installer 2025.10.3! There are no changes in this version besides upgrade to the latest Home Assistant.
Hass Core Installer is a free and open source tool that helps you install and manage Home Assistant Core using the manual installation method. Even though this method is now officially deprecated, I know some people still prefer it for its flexibility and control.
You can find the project and source code here: https://github.com/zikusooka/hass-core-installer
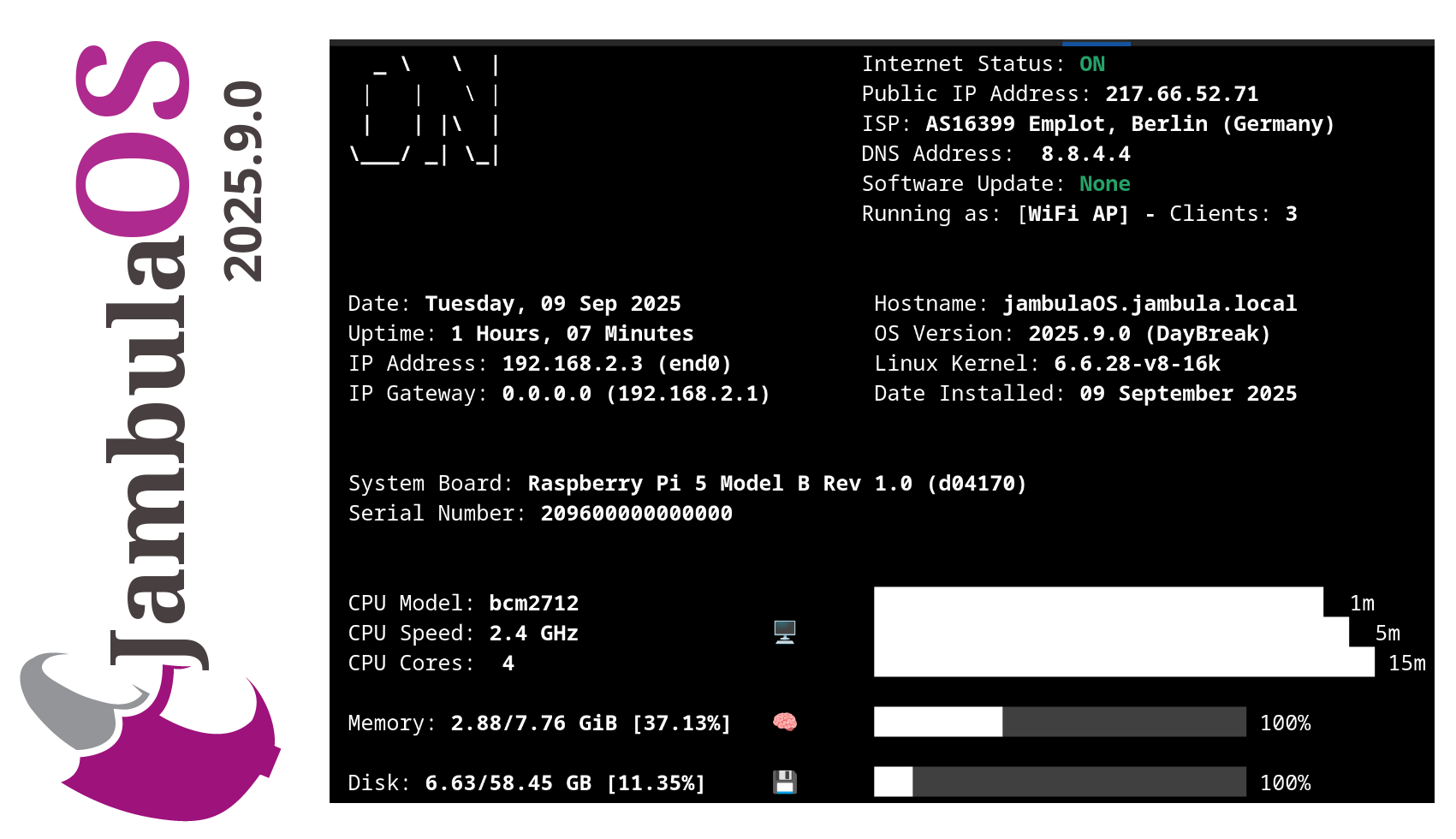
Jambula OS 2025.9.0 Released – Now with Bluetooth Speaker Support!
I have uploaded the latest 𝐉𝐚𝐦𝐛𝐮𝐥𝐚 𝐎𝐒 image – version 𝟐𝟎𝟐𝟓.𝟗.𝟎. This release continues the work I have been doing to make Jambula OS, a reliable, lightweight Linux platform for embedded SoC devices like the Raspberry Pi 5. So if you are building smart automation solutions on embedded platforms, this update is definitely worth checking out.
𝐇𝐢𝐠𝐡𝐥𝐢𝐠𝐡𝐭𝐬 𝐢𝐧 𝐭𝐡𝐢𝐬 𝐫𝐞𝐥𝐞𝐚𝐬𝐞:
𝐁𝐥𝐮𝐞𝐭𝐨𝐨𝐭𝐡 𝐬𝐩𝐞𝐚𝐤𝐞𝐫 𝐬𝐮𝐩𝐩𝐨𝐫𝐭: Added support for Bluetooth audio devices which is ideal for voice prompts or music output.
𝐒𝐰𝐢𝐭𝐜𝐡𝐞𝐝 𝐭𝐨 𝐊𝐞𝐚 𝐃𝐇𝐂𝐏: Replaced dnsmasq with 𝐊𝐞𝐚 𝐃𝐇𝐂𝐏 for better dynamic addressing management.
𝐖𝐢𝐅𝐢 𝐡𝐨𝐭𝐬𝐩𝐨𝐭 𝐜𝐥𝐢𝐞𝐧𝐭 𝐜𝐨𝐮𝐧𝐭 𝐢𝐧 𝐌𝐎𝐓𝐃: See how many clients are connected to your hotspot right in the system’s MOTD.
𝐐𝐑 𝐜𝐨𝐝𝐞 𝐨𝐧 𝐢𝐧𝐢𝐭𝐢𝐚𝐥 𝐥𝐨𝐠𝐢𝐧: Displays a QR code linking to vendor/device info, useful for branding or support.
𝐈𝐦𝐩𝐫𝐨𝐯𝐞𝐝 𝐬𝐞𝐭𝐮𝐩 𝐭𝐨𝐨𝐥𝐬: Smoother first-time setup experience with updated scripts.
𝐇𝐨𝐦𝐞 𝐀𝐬𝐬𝐢𝐬𝐭𝐚𝐧𝐭 𝐮𝐩𝐝𝐚𝐭𝐞𝐝: Latest Home Assistant version included to keep your platform up to date.
𝐁𝐮𝐠 𝐟𝐢𝐱𝐞𝐬: Minor fixes including firewall and weather integration improvements.
𝐋𝐞𝐚𝐫𝐧 𝐦𝐨𝐫𝐞 𝐚𝐛𝐨𝐮𝐭 𝐉𝐚𝐦𝐛𝐮𝐥𝐚 𝐎𝐒:
https://code.jambula.net/zikusooka/Jambula-OS
Hass Core Installer 2025.9.0 Released
I have released Hass Core Installer 2025.9.0! There are no changes in this version besides upgrade to the latest Home Assistant.
Hass Core Installer is a free and open source tool that helps you install and manage Home Assistant Core using the manual installation method. Even though this method is now officially deprecated, I know some people still prefer it for its flexibility and control.
You can find the project and source code here: https://github.com/zikusooka/hass-core-installer
Announcing Jambula OS Linux Version 2025.6.0 – Now Available!
I’m excited to share that the latest image of Jambula OS Linux – Version 2025.6.0 is officially live!
This small, maintenance-focused update wraps up important improvements as I look ahead to a week full of fresh open source ideas, conversations, and community engagement.
Why Jambula OS?
Jambula OS is a lightweight, flexible Linux distribution optimized specifically for Raspberry Pi and other low-power, SoC-based edge devices. It’s designed with performance, stability, and adaptability in mind, making it the perfect foundation for embedded systems and automation projects at the edge.
My vision? To make Jambula OS the go-to platform for innovators building smart home and office automation hubs. Ambitious? Absolutely. But innovation thrives on ambition!
What’s next?
With this update complete, I will soon begin preparations for the next major release. Stay tuned for exciting new features and enhancements that will continue to empower developers and creators alike.
Download the latest Jambula OS image here:
https://github.com/zikusooka/Jambula-OS
Exciting times are ahead. Let’s keep building the future together!
Hass-Core-Installer: Keeping Home Assistant Core Alive
It is finally happening – Home Assistant Core, along with other legacy installation methods and 32-bit system support, is officially being deprecated. The Home Assistant team announced this major shift in their recent blog post, signaling the end of an era for many longtime users who have relied on Core and Supervised installs for years. Starting with the 2025.12 release, support for these installation methods and older architectures like i386, armhf, and armv7 will be phased out.
For most users, the path forward is clear: migrate to Home Assistant OS or Home Assistant Container. These methods offer a streamlined, more stable experience with ongoing official support. But what about those of us who love the flexibility and control that Home Assistant Core provides? Or those running on hardware that does not fit the new supported architectures?
Hass-Core-Installer to the rescue
If you are a developer or among the few who want to continue running Home Assistant Core despite the official deprecation, there’s no need to despair! I created Hass-Core-Installer, a free and open source tool designed to help you install and maintain Home Assistant Core on your own terms. The latest offline version supported is 2025.5.3.
Hass-Core-Installer is a practical, easy-to-customize script for users who want to keep using Core without relying on official support. Whether you are a developer, hobbyist, or power user, this tool helps you to keep your Home Assistant setup running smoothly, even as the official landscape changes.
Why Hass-Core-Installer?
- Flexibility: Retain full control over your Home Assistant environment.
- Compatibility: Continue using Core on your preferred hardware, including some 32-bit systems.
Ready to Keep Your Home Assistant Core Setup?
If you want to learn more and why I created it, visit my blog post here: Hass-Core-Installer or if you’re ready to try it, go to GitHub where you will find everything you need to install Home Assistant Core confidently and keep it running well beyond the official end-of-life.
While the Home Assistant project moves forward with new priorities, the spirit of customization and hands-on control lives on through projects like Hass-Core-Installer. If you are passionate about Home Assistant Core, this is your chance to stay ahead and keep your smart home running your way.
An Alternative Way to Install Home Assistant Core
Hass-Core-Installer Version 2025.5.1 Released
Official support for installing Home Assistant Core, Supervised, and some other methods will soon end (see announcement). If you still want to run Home Assistant Core on your own hardware, I have good news!
I’ve released a new and improved version of hass-core-installer. This tool makes it easy to install Home Assistant Core on many types of systems, including ARM64 devices like Raspberry Pi 5.
You can try it now by visiting the GitHub page.
Why Use Hass-Core-Installer?
- Works on Many Systems: Supports most system types, especially ARM64.
- Works Offline: You can install Home Assistant Core even without an internet connection.
- Future-Proof: Keeps working even after official support ends.
- For Power Users: Best for people who already know how to set up Home Assistant.
What’s New in Version 2025.5.1?
- Upgrade Home Assistant to the latest version
Updated Home Assistant Core to the latest version of 2025.5.1 - Faster Installs with uv:
The installer now uses uv, a new and very fast Python package manager. This means Home Assistant installs faster and package problems are easier to fix.
(Learn more about uv here). - Supports More Python Versions:
You can now use different versions of Python. By default, it uses Python 3.13.3. - Better Troubleshooting:
Improved tests and logging help you find and fix problems more easily.
How to Get Started
- Go to the hass-core-installer GitHub page.
- Follow the instructions to download and use the tool.
If you’re an experienced Home Assistant user and want to keep running it your way, give hass-core-installer a try! Your feedback and suggestions are welcome on GitHub.